What were the most significant data breaches in 2019? Will ransomware still be a threat in 2020? (Spoiler alert: It’s forecast to be worse than ever.) Which industries were attacked most?
We have put together a shortlist of overview articles, surveys, and posts worth returning to for use as a quick reference to consult in 2020.
Cnet’s Rae Hodge revisits the biggest data breaches of the past year, and she has two words for readers: “unsecured database.” Two years after we posted this, security researchers report more unintentional leakage than ever in 2019.
According to Risk Based Security, (reported) breaches were up 33% over 2018, with a total of 7.9 billion exposed records. As early as in November, the research firm labeled 2019 the "worst year on record."

The American Bar Association conducts an annual Legal Technology Survey, which culminates in a report on attorney’s use of technology. John G. Loughnane, a partner with Nutter McClennen & Fish LLP in Boston, MA, discusses 2019 Survey results related to cybersecurity and what they mean for law firms.
More than a third of respondents (36%) reported their firms had been infected with spyware or malware. More than a quarter (26%, mostly in larger firms) were unaware whether any such infection has ever occurred.
One malvertising campaign alone, eGobbler, distributed more than a billion malware-spiked ads and spam via online advertising networks in 2019. Unsuspecting visitors of popular websites are the victims, and - by extension - the companies they work for.
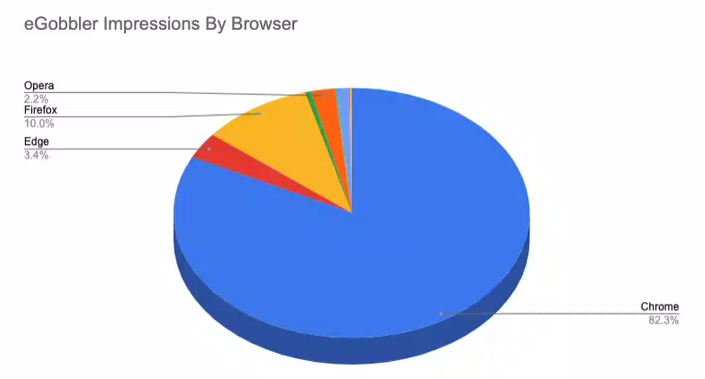
Source: Confiant
“The rapidly evolving tactics of top threat actors, who skillfully identify and exploit browser vulnerabilities to generate redirects even in the presence of iframe sandboxing, show that this is not a problem that is going away any time soon,” concludes ad security firm Confiant in its Demand Quality Report for Q3 2019.
Cybercriminals are shifting their focus to the public sector. Ransomware hit at least 948 government agencies (including schools and healthcare providers) in 2019, according to a comprehensive report by security firm Emsisoft.
Experts estimate the potential damages at more than $7.5 billion. Does your organization have what it takes to prevent ransomware?
Cybersecurity firm Coronet published its annual Cybersecurity in the City report in December, with a focus on Where Small Businesses Are Most Vulnerable to Attack. The underlying research analyzed the threats and vulnerabilities to small and mid-market businesses within the 50 largest cities in the US.
The security researchers based their ranking on an analysis of one million endpoints (all major operating systems), 24 million networks (public and private), 320,000 SaaS accounts (Dropbox, Box, Slack, and Salesforce), and 270,000 Gmail and Office 365 email accounts.
For the second year in a row, Las Vegas was identified as the nation’s least cyber-secure metro, followed by Houston and New York City. Salt Lake City, St. Louis, and Seattle–Tacoma ranked as the least vulnerable cities to cyberattack.
As if healthcare bills weren’t high enough, the past year saw more medical care disrupted and patients exposed to medical identity theft (we explain how it works in this post) than ever before.
Part of this development was due to the resurgence of targeted ransomware attacks against hospitals, medical practices, and nursing homes across the nation.
Also to blame are third-party vendor breaches and phishing, which caused some of the most massive healthcare data breaches of the past year, reports Jessica Davis in her overview on Health IT Security, Cyber Threats Behind the Biggest Healthcare Data Breaches of 2019.
Background: Digital medical records are worth much more on the black market than, for example, stolen credit card information. And other than with credit card theft and bank fraud, individual victims - you and I - are left holding the bag, as we’ve explained here.
So if you went to seek medical treatment in 2019, don’t be surprised if at some point in the future you get hit out of nowhere with the medical bills for, say, some narco cartel member’s plastic surgery in your name, at your expense.
What’s the ROI of threat hunting? That was one of the core questions raised by the SANS 2019 Threat Hunting Survey.
The answer may lie in a strategy and tool selection that avoids mission creep and results in measurable effects (read: savings and significantly reduced incident rate) to prove it.
The SANS paper provides a snapshot of the different needs and challenges within organizations with recent and mature cyber threat hunting programs.
As for the newest and coolest threat hunting software introduced or refined in 2019, check out these comprehensive reviews of top tools for threat hunters from Black Hat USA 2019 on our blog.
Canada-based eSentire, a global vendor of cloud-delivered threat detection and response solutions, just presented its Annual Threat Intelligence Report: 2019 Perspectives and 2020 Predictions.
According to the report, Emotet malware accounted for almost 20% of confirmed malware incidents this past year. The modular banking Trojan is considered one of the most costly and destructive malwares affecting private and public sectors, with new iterations much in demand on the black markets of the Dark Web.
The authors highlight “a need for zero trust” online (we agree), as cybercriminals increasingly hone their micro-social engineering skills to exploit the trust circle and supply chains of their target victims, for example by posing as trusted vendors.
"We have found several cases of surprisingly large organizations with valuable data and critical infrastructure,” said Research Lead Keegan Keplinger, “with little more than an anti-virus program running on their endpoints.”
Let that ↑ sink in.
This year, we better brace for more bad news from companies and public sector organizations who are still responding to cyber threats 1990s-style. That is, on their own turf and when it’s too late - after their IT perimeters have already been breached.
Instead of, you know - insulating themselves from such threats with cloud-based web isolation, which isolates any web-borne code - whether potentially harmful or not, or who knows? - safely offsite, 2020-style.
Going into this new year, it’s a thing, and it's been one for a while already for the world’s most security-sensitive private and public sector organizations, which use Authentic8’s Silo and Silo Research Toolbox web isolation technology.
Looking back on 2019’s data breaches and fake security trends, it's likely to become even more obvious in hindsight why that makes sense.